Digital Vulnerability Program
Total Privacy. Absolute Vigilance.
Stay safe from online threats. We review your online presence, identify points of vulnerability, and remove personal information that puts you at risk.

Being Online Shouldn't Mean Being at Risk
We believe vulnerability shouldn’t be the price of living in a connected world. Today, risk goes far beyond exposed addresses and phone numbers. It’s in metadata, geotags, and social connections. It’s in online behavior patterns, leaked credentials, forgotten accounts, and personal affiliations that can be traced, linked, or exploited. A photo reveals location habits. A donation discloses political leanings. A family member’s profile opens a backdoor.
Hetherington Group exists to break that chain. By identifying what’s exposed, removing what shouldn’t be public, and helping people understand how digital breadcrumbs turn into real-world threats, we restore control, reduce fear, and protect what matters most - people, families, reputations, and livelihoods.
Our Digital Vulnerability Program removes the digital footprint that creates risk. With the trusted expertise of Hetherington Group and the exclusive deletion technology of 360 Privacy, this is next-level digital safety for those who cannot afford exposure.

The Risk to Executives, High-Worth Individuals and Entertainers Goes Beyond Physical Threats

According to the Digital Risk Index 2025, a survey conducted by IAPP, respondents identified that the top risk to organizations is the risk to privacy and data protection.
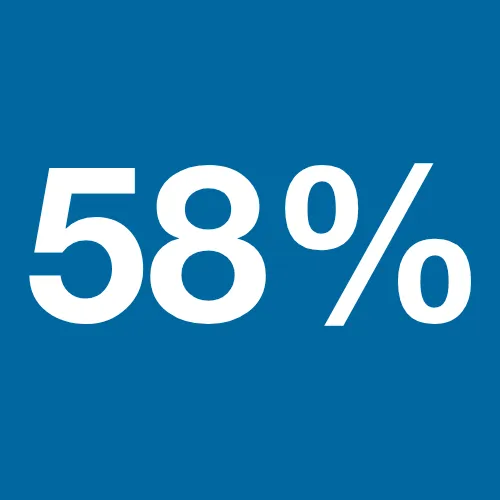
In a 2021 Research Report by Ontic, 58% of respondents said their CEO had received physical threats after taking a position on a racial and/or political issue.

Roughly 11.7 million adults in the United States have been doxed or had their personal information maliciously exposed online.
A Proven Three-step Approach to Keep Personal Information Private

1. Assessment
We search online sources to find exposed personally identifiable information (PII) such as addresses and contact information, personal relationships and associates, locations, and login credentials. This assessment can include family members to find any additional digital privacy vulnerabilities.

2. Removal
We remove as much personally identifiable information (PII) as possible such as residential address, personal phone number, and email addresses for the subject and family members within the residence. Plus, we'll help update privacy settings and provide best practices for recognizing privacy risks and how to keep information private online.

3. Monitoring
As part of this subscription service, we will continuously monitor the subject's PII online for new exposures and remove them if found. If a risk is found involving cyber criminals, or if the subject wants to manage their identity and be in control of their privacy on an ongoing basis, this service will help keep personal information safe from online threats.
Finding & Removing Personally Identifiable Information (PII) Found on the Internet
Opt Out to Keep
Your Information Private
Surveillance is no longer an occasional intrusion or something we tolerate in times of crisis. It has become the oxygen of the digital world. When this guide was first written in 1998, the internet was young. The threats to privacy came from credit bureaus, direct marketers, and the first data brokers. By 2020, the pandemic accelerated our acceptance of surveillance with cameras, apps, and databases justified in the name of public health.
This guide will teach you how to:
- Opt out of databases that contain your name, address, phone number, and other publically available data
- Opt out of DNA databases
- Understand how data is collected about your through websites and apps
- Stay safe and vigilant about online data exposure

Testimonials
Mike,
Beacon Transport

“I love it that you gave us methods that are ethical AND easy … You really did make me think—and begin to shift the way I think—about how I do my job vetting the individuals and the companies we work with.”
Joan,
Founder, Principal & Analyst, Sullivan Research, LLC

“HG is the best source for acquiring investigative knowledge and skills. Highly recommend.”
Bruce Sackman,
SPI President

“Cynthia is the undisputed, undefeated champion of open source intelligence. She is the number one go-to person for both training and actual research to collect electronic evidence and investigative leads from the Internet.”
Expert Investigations and Intelligence
sales@hetheringtongroup.com
(973) 706-7525
593 Ringwood Ave, Wanaque, NJ 07465
© 2026 Hetherington Group - All Rights Reserved
© 2026 Hetherington Group - All Rights Reserved | Privacy Policy | Terms & Conditions

